Physical Layer Security Enhancement With Reconfigurable Intelligent Surface-Aided Networks
Published in IEEE Transactions on Information Forensics and Security, 2021
Recommended citation: Jiayi Zhang, Hongyang Du, Qiang Sun, Bo Ai, and Derrick Wing Kwan Ng, "Physical layer security enhancement with reconfigurable intelligent surface-aided networks," IEEE Transactions on Information Forensics and Security, vol. 16, pp. 3480-3495, May 2021. https://ieeexplore.ieee.org/document/9439833
Abstract: Reconfigurable intelligent surface (RIS)-aided wireless communications have drawn significant attention recently. We study the physical layer security of the downlink RIS-aided transmission framework for randomly located users in the presence of a multi-antenna eavesdropper. To show the advantages of RIS-aided networks, we consider two practical scenarios: Communication with and without RIS. In both cases, we apply the stochastic geometry theory to derive exact probability density function (PDF) and cumulative distribution function (CDF) of the received signal-to-interference-plus-noise ratio. Furthermore, the obtained PDF and CDF are exploited to evaluate important security performance of wireless communication including the secrecy outage probability, the probability of nonzero secrecy capacity, and the average secrecy rate. Monte-Carlo simulations are subsequently conducted to validate the accuracy of our analytical results. Compared with traditional MIMO systems, the RIS-aided system offers better performance in terms of physical layer security. In particular, the security performance is improved significantly by increasing the number of reflecting elements equipped in a RIS. However, adopting RIS equipped with a small number of reflecting elements cannot improve the system performance when the path loss of NLoS is small.
Index Terms: Fisher-Snedecor F-distribution, MIMO, reconfigurable intelligent surface, stochastic geometry.
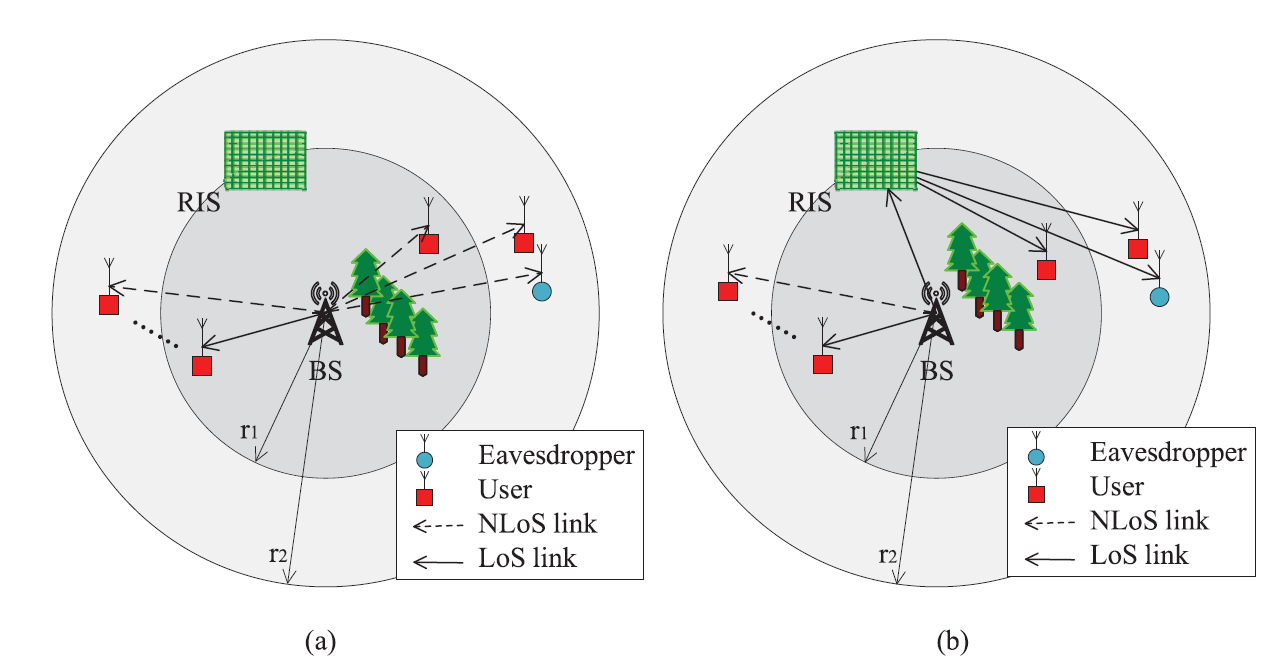
Fig. 1: Two practical scenarios: Communication without (left hand side) and with RIS (right hand side).
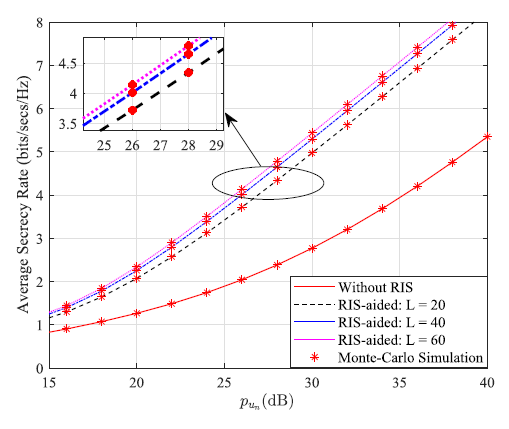
Fig. 7: Average security rate versus transmit power for user n.
